Adversary Simulation made easy
MACAT is the Malware and APT Collection and Attack Tool.
Simulate Threat Actor activities to test and improve your cybersecurity defenses
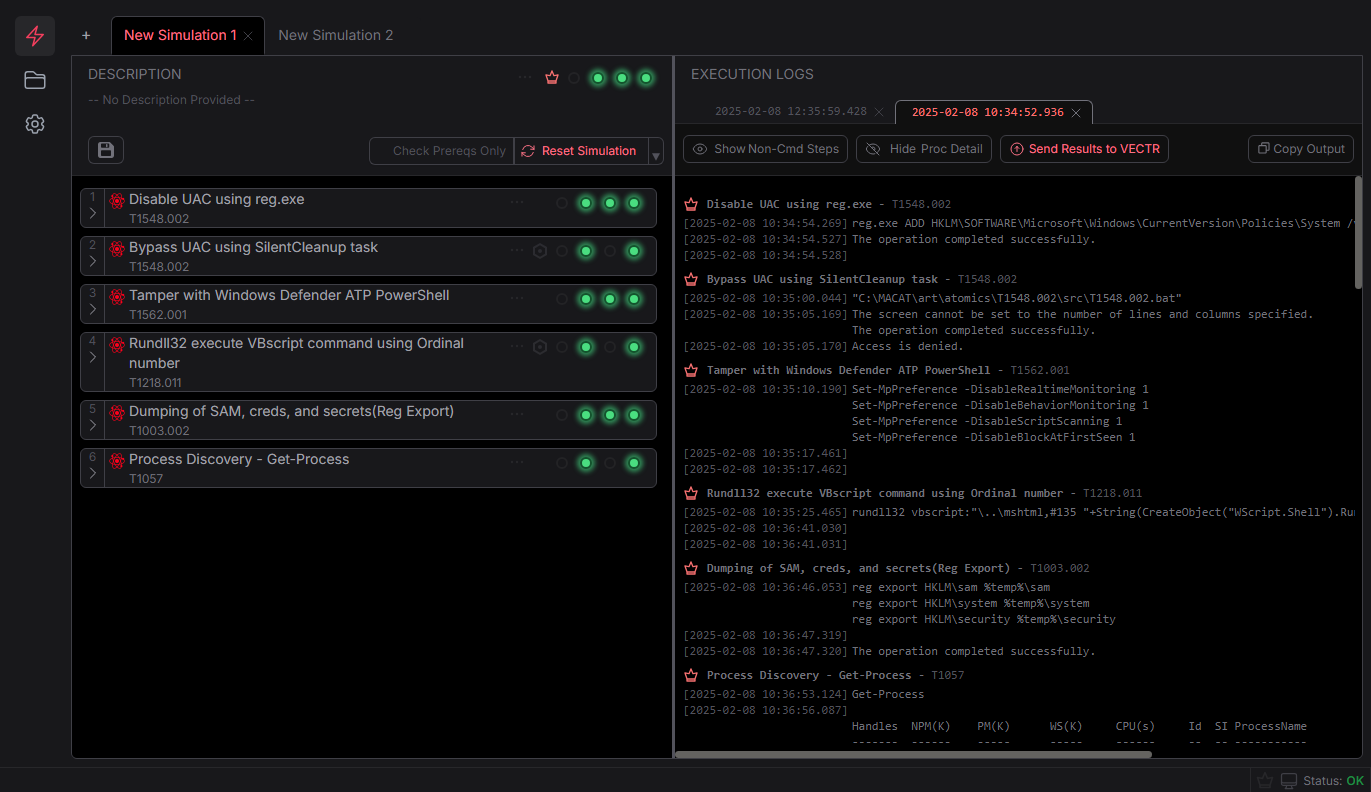
Execute faster and easier
Everything you need
to Accelerate
your Threat-Informed Defense program
- Expandability
-
MACAT supports existing industry standard file formats which makes for simple expansion of executable content.
- Results Tracking
-
Automatically save a detailed record of every adversary simulation execution for log review and result comparison.
- Data Sharing
-
Data sharing is a first-class feature. Load, save, and share data in the MACATable TOML data format or use the Atomic Red Team YAML format.
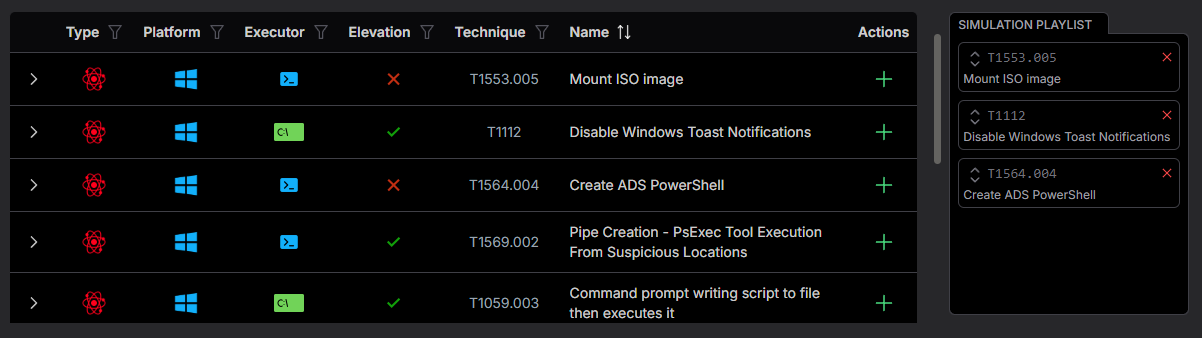
Quick Start
Automatic Content Synchronization
Immediate access to thousands of adversary procedures from Atomic Red Team and other community threat repositories
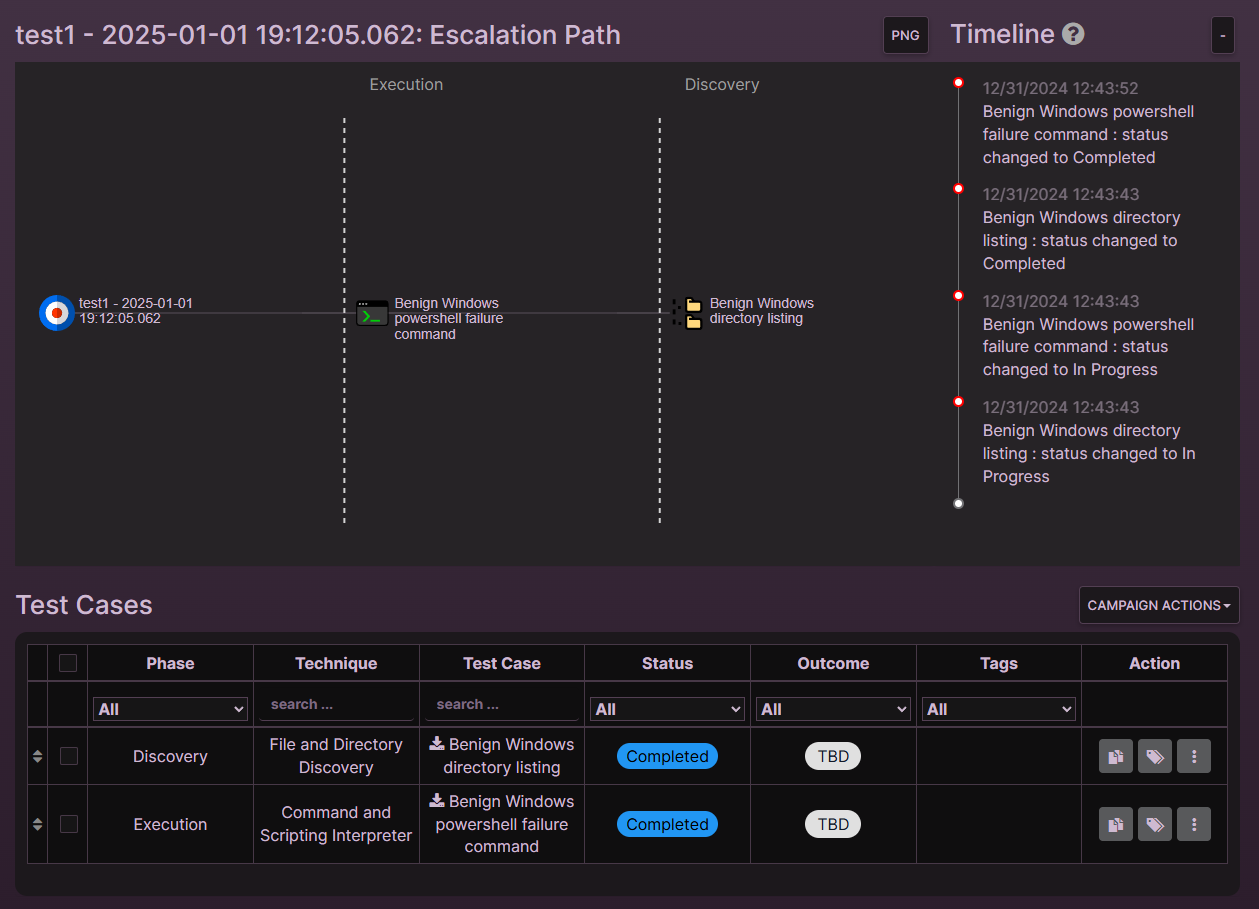
Integrations
Track Your Results
Send MACAT output directly to a VECTR instance
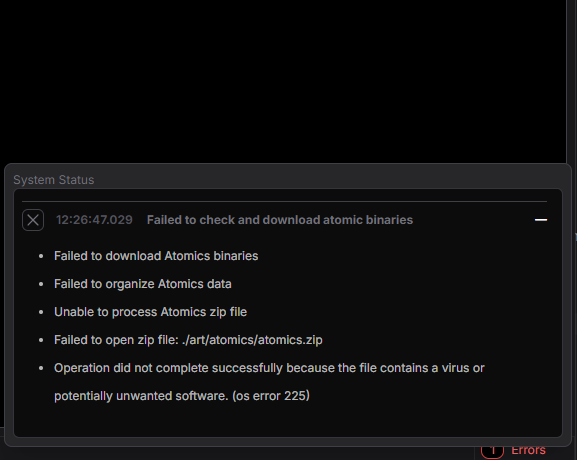
Troubleshooting
Easy Recovery
MACAT has built-in error reporting and status indicators to correct issues when running adversary simulations
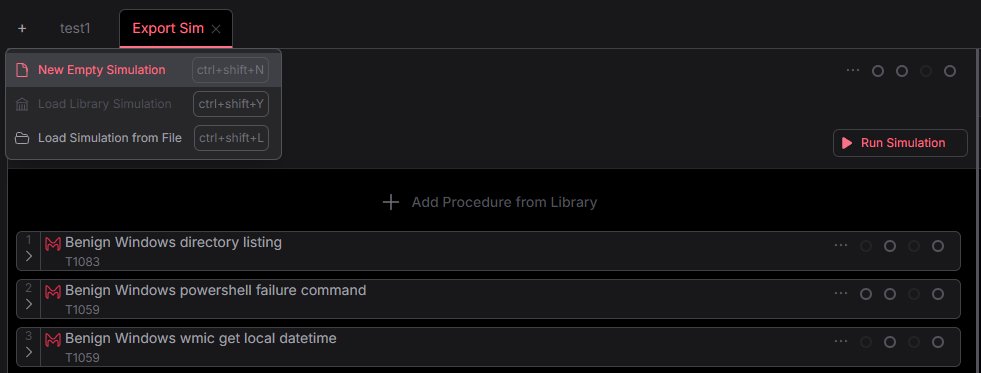
Management
Save / Load Custom Simulations
Content is managed in easily modifiable text files, perfect for source control or sharing
Compatability
MACAT is compatible with purpose-built cybersecurity tools focused on solving specific problems. Many organizations struggle implementing, scaling, and learning complex automations or other adversary simulation tools.
MACAT starts with the basics to help you and your team learn and grow.